You know from previous post that SecurityFilterChain determines which requests go through the filter chain, so how does SecurityFilterChain match to a specific request?
How to intercept specific requests
Only requests that satisfy the match method of a SecurityFilterChain can be processed by that SecurityFilterChain, so how do you configure a SecurityFilterChain to process a specific path?
RequestMatcher
HttpSecurity has a built-in RequestMatcher property to handle path matching. The RequestMatcher can be summarized in the following categories.
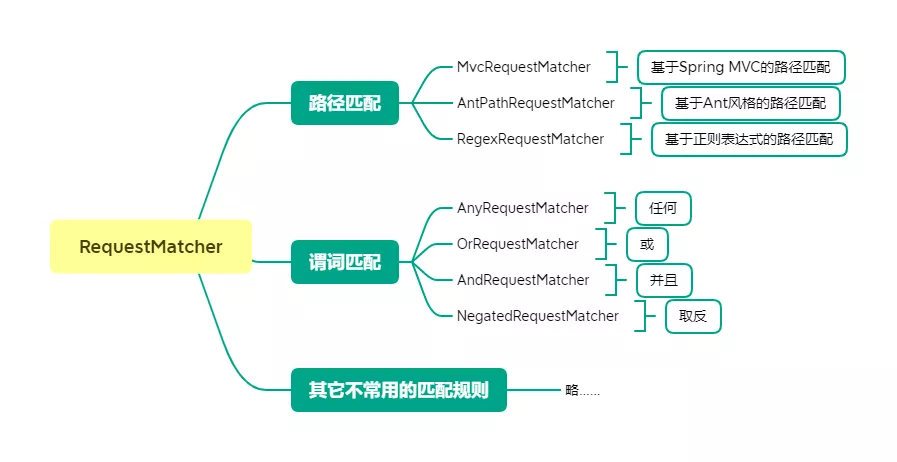
Use the Ant path.
|
|
If you configure a global Servlet Path such as /v1, configure the ant path as /v1/foo/** to be consistent with the MVC style.
|
|
Also MVC style can automatically match suffixes, for example /foo/hello can match /foo/hello.do, /foo/hello.action and so on. Alternatively you can use regular expressions for path matching.
|
|
If the above doesn’t meet your needs, you can customize the matching rules with the HttpSecurity.requestMatcher method; if you want to match multiple rules, you can freely combine the matching rules with the HttpSecurity.requestMatchers method, like this.
Once you configure the path matching rule, you will find that the default form login 404 is not accessible because the default is
/login, which you can’t access after adding the prefix.
Usage Scenarios
For example, if your backend management system and frontend application each take a different filter chain, you can configure the respective filter chain based on the access path. For example.
|
|
Also use this feature to reduce coupling between different rule URIs.
Think about how HttpSecurity, a Spring bean, can be reused.
Reference
https://mp.weixin.qq.com/s/W_N-il-IIFaXI7_YZp1zFQ