This article will further experience Keycloak, give us an intuitive understanding of it, and then go deeper and deeper to break down its design concepts and ideas.
General idea
Since we already know beforehand that Keycloak provides an adapter for Spring Security. Let’s first get the core concepts of Keycloak clear independently and then work on how it incorporates Spring Security.
Installing Keycloak
The Keycloak version for this article is
14.0.0.
I have never liked to waste time on installation, and it is most convenient to be able to use Docker for the research phase.
|
|
Execute the above command to install Keycloak , after success open http://localhost:8011/auth/admin enter the account admin and password admin , you will enter the management console. If you feel uncomfortable with English, you can change it to Chinese according to the following chart.
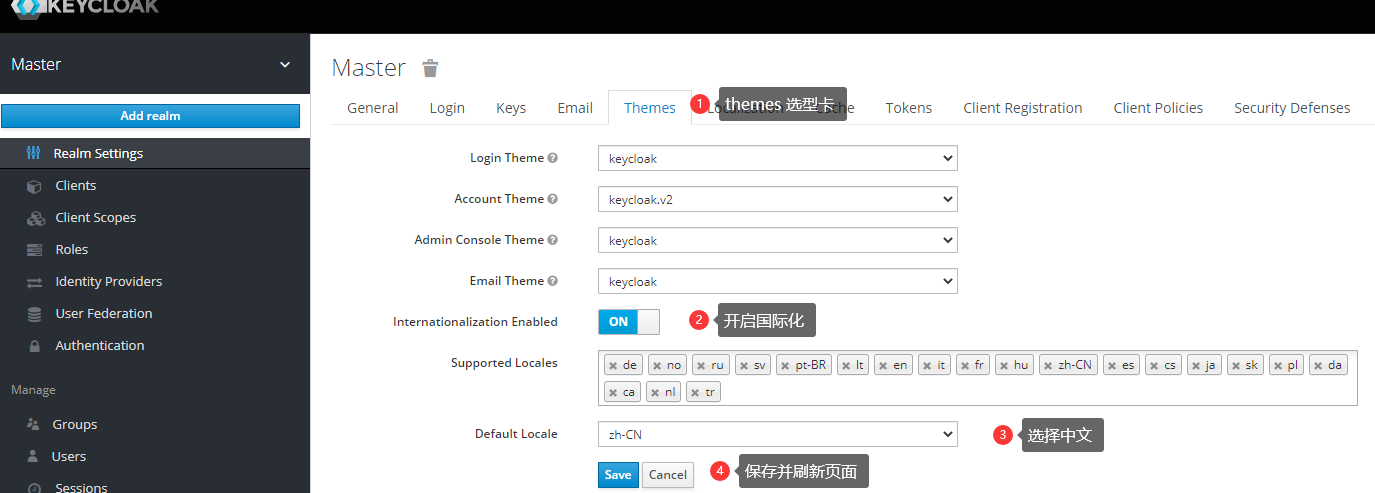
After the change you click on random columns to understand, imagine their respective functions and roles, this time you have to relax a little without thinking too deeply, just to understand the whole picture.
Realm
If you’ve come across the well-known security framework Shiro I’m sure you’re not unfamiliar with this concept. realm is a space to manage users and corresponding applications, a bit of a tenant flavor that allows the ability to maintain logical isolation between different realm.
By default, Keycloack provides a realm called Master that does not take care of the management of specific applications and users, it is only used to manage the lifecycle of other realms.
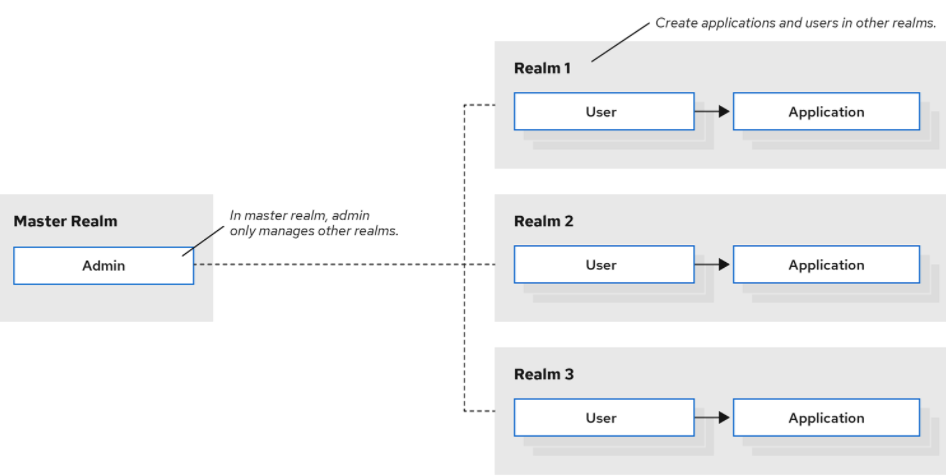
Log in to realm of Master to create a custom domain felord.cn.
User
A User is an entity that can log in to the application and can actually be understood as an account. They can have attributes associated with themselves, such as email, username, address, phone number and birthday. They can be assigned group memberships and have specific roles assigned to them. The Users in Keycloak have their subordinate realm. Next, create a new user in my custom domain felord.cn above by
- Find Administration->Users in the menu bar, then open Add User.
- Type in the unique required field
username. - Turn on (
ON) email authentication (Email Verified) and save. - Click the Credentials tab to set a temporary password for the new user. This password is temporary and the user will need to change it the first time they log in. If you prefer to create a permanent password, toggle the Temporary switch to Close and click Set Password .
Then log out of the current user admin and go to http://localhost:8011/auth/realms/felord.cn/account and log in to the felord.cn domain as the user felord you just created.
Did you find the characteristics of the login link?
Here the process of creating a realm and account is finished, but I believe most people are still confused when they see this. How to do it manually? Do not worry later will be combined with the code to achieve the above process and more in line with the application scenario process.
Keycloak core concepts
Next are some concepts we need to master when using Keycloak, we have already mentioned realm and user above, so we won’t go over them here
authentication
The process of identifying and authenticating users. Proves that “you are who you say you are”.
authorization
The process of granting access to a user. Indicates “what you can and can’t do”.
credentials
Credentials that prove the user’s identity. This may be a password, a one-time password, a digital certificate, or a fingerprint.
roles
Roles are an important concept in RBAC and are used to indicate the type of identity of a user.
user role mapping
User role mapping relationships. Often a user may have multiple roles, and a role may correspond to different people.
composite roles
Composite roles, as arcane as it sounds, are actually subordination or inheritance relationships of roles. The B role is subordinate to the A role, so if you have the A role, you must have the privileges of the B role.
groups
User groups, you can give a series of roles to a defined user group, once a user belongs to that user group, then that user will get all role permissions of the corresponding group.
clients
clients. Usually refers to applications or services that need to request keycloak to authenticate a user, or even requesting entities that seek keycloak protection and are registered with keycloak are clients.
client adapters
keycloak has adapters designed to support multiple languages and cross-platforms, such as those for Java and those for Python. Some of them are built-in implementations, others need to be implemented according to the abstract definition of keycloak. We’ll be dealing mainly with Spring Boot Adapter.
identity provider
The service used to authenticate users, referred to as IDP. keycloak is itself an IDP. This is similar to the AuthenticationProvider interface in Spring Security.
There are a few more concepts that I will add when I encounter them, a bit more to digest first.
Summary
Today’s article mainly provides a preliminary experience of keycloak, builds a development environment for subsequent learning, and summarizes some core concepts of keycloak. However, due to the limitation of space, we did not completely sort out some concepts, but learning is gradual and cannot be rushed. With the custom realm and users built, I will try to use keycloak to protect Spring Boot applications in the next article.
Reference
https://felord.cn/keycloak-1.html